Endpoint Security EDR,XDR&MDR
Endpoint security refers to the practice of securing endpoints—such as computers, mobile devices, and servers—on a network. It aims to protect these devices from cyber threats like malware, ransomware, and unauthorized access.
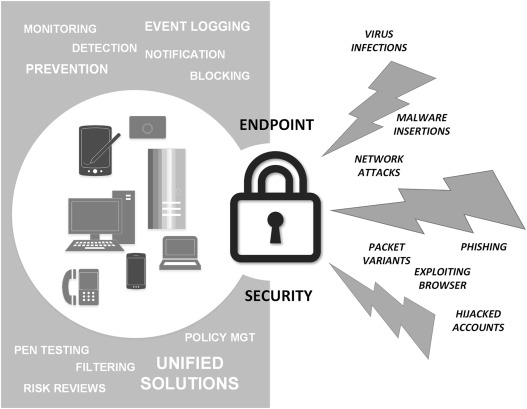
Major Features:
-
Threat Detection
-
Antivirus and Antimalware
-
Firewall Protection
-
Data Encryption
-
Access Control
-
Device Control
-
Centralized Management
-
Reporting and Analytics
Deployment Model:
-
Deploying Identity & Access Management on-premises.
-
Deploying Identity & Access Management in the cloud.
-
Deploying a hybrid Identity & Access Management platform.
Our Offering:
- Sophos
- CrowdStrike
- Cortex XDR
- Trend Micro
- Microsoft
- KasperSky


